AI & ML monitoring
Intelligent change tracking and threat detection.
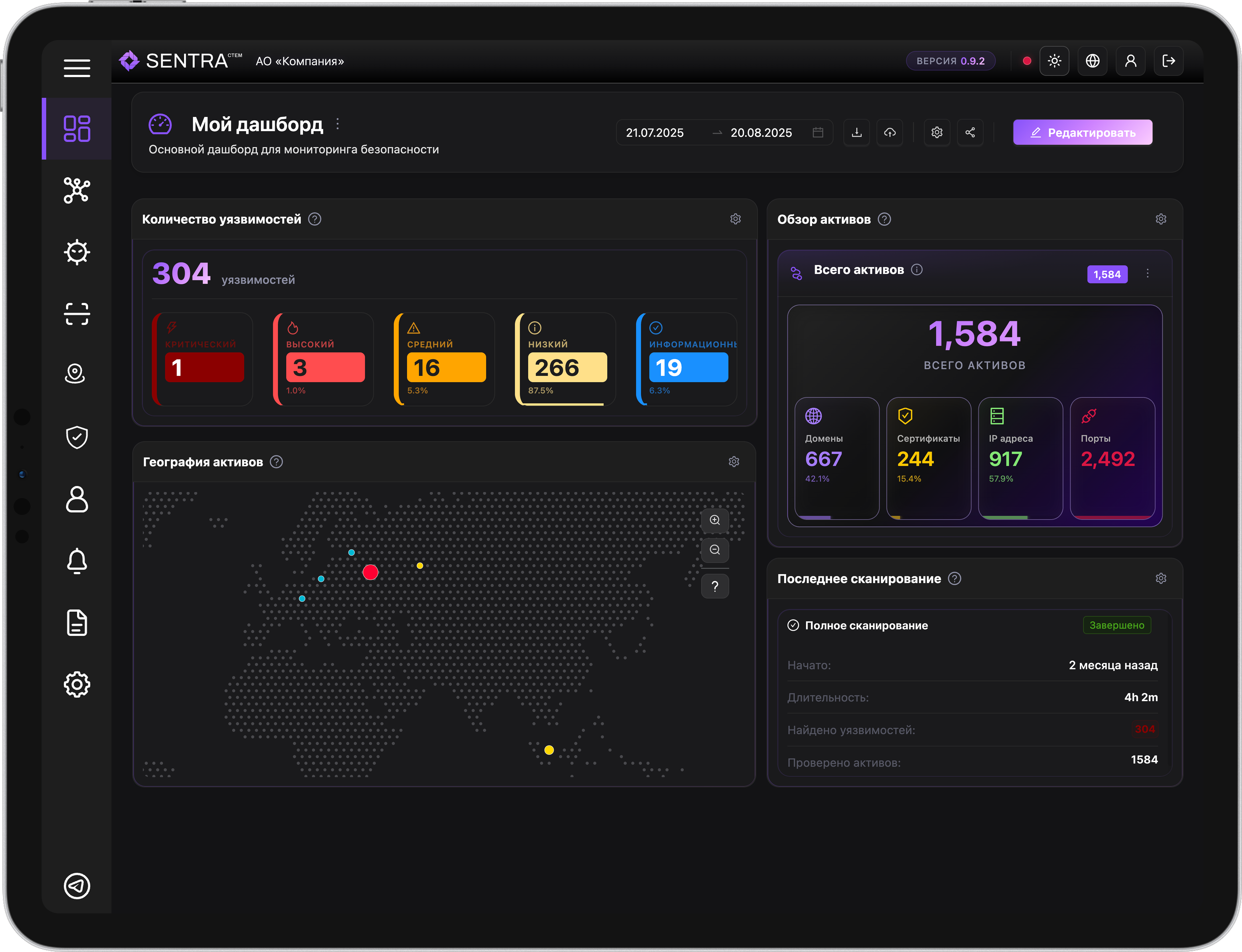
Gain full control over your external attack surface
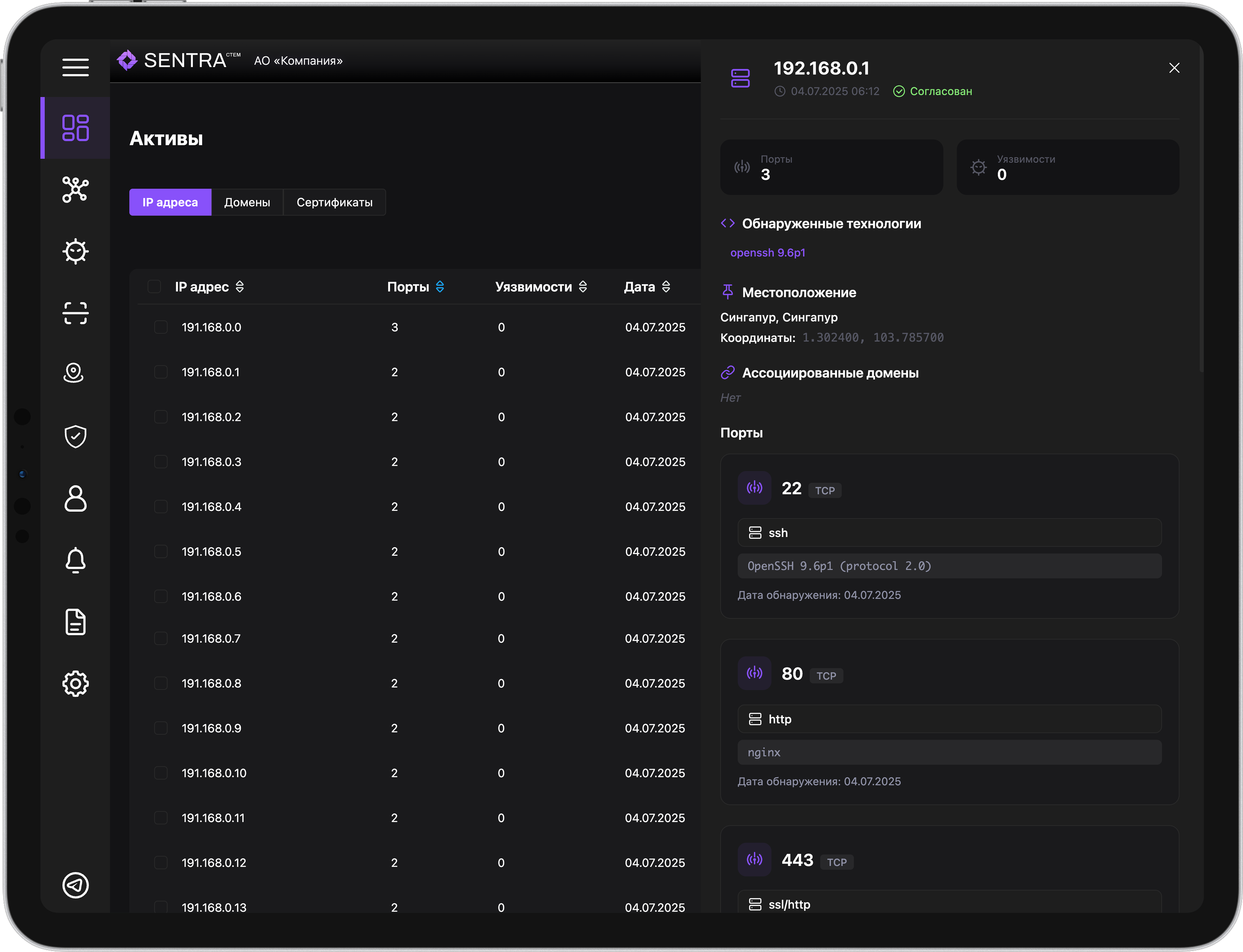
We discover all assets, including shadow and forgotten
No false positives after ML filtering and manual verification
Reduce the average vulnerability lifetime on the perimeter from the first week
Intelligent change tracking and threat detection.
Fast, flexible scanning of any infrastructure.
Red Team assists in analyzing and fixing vulnerabilities.
Years of pentesting and Bug Bounty experience in one solution.
Focus only on critical business risks.
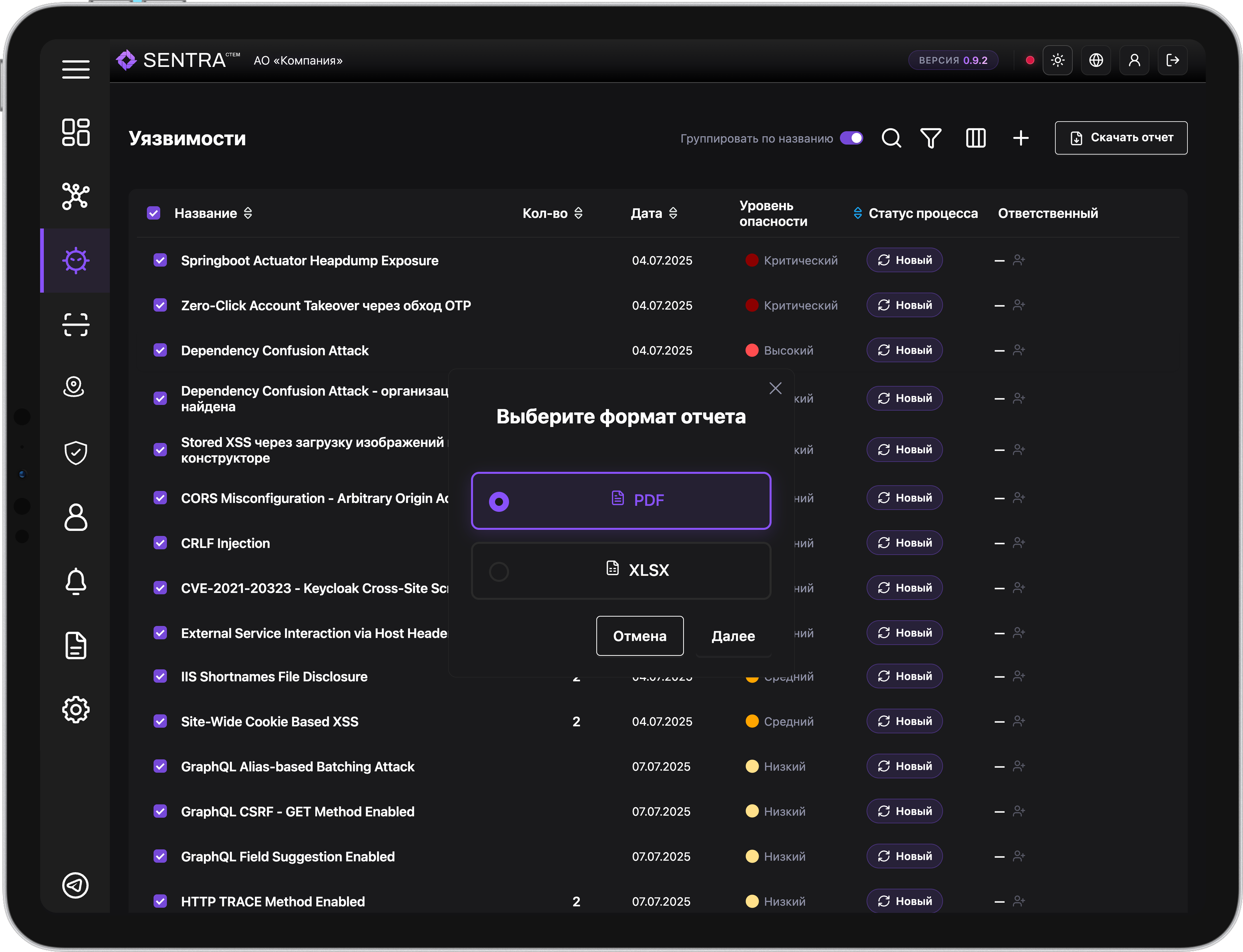
Manual and automated verification of vulnerability fixes.
Continuous Threat
Exposure Management
Continuous automated discovery of all digital assets (including shadow assets). Building a complete and up-to-date map of the infrastructure.
International security and IT certifications

.svg)
.svg)
.svg)
.svg)
.svg)

.svg)
.svg)
.svg)
.svg)
.svg)
Bug Bounty program participation
.svg)
.svg)
.svg)
.svg)
.svg)

.svg)
.svg)
.svg)
.svg)
.svg)

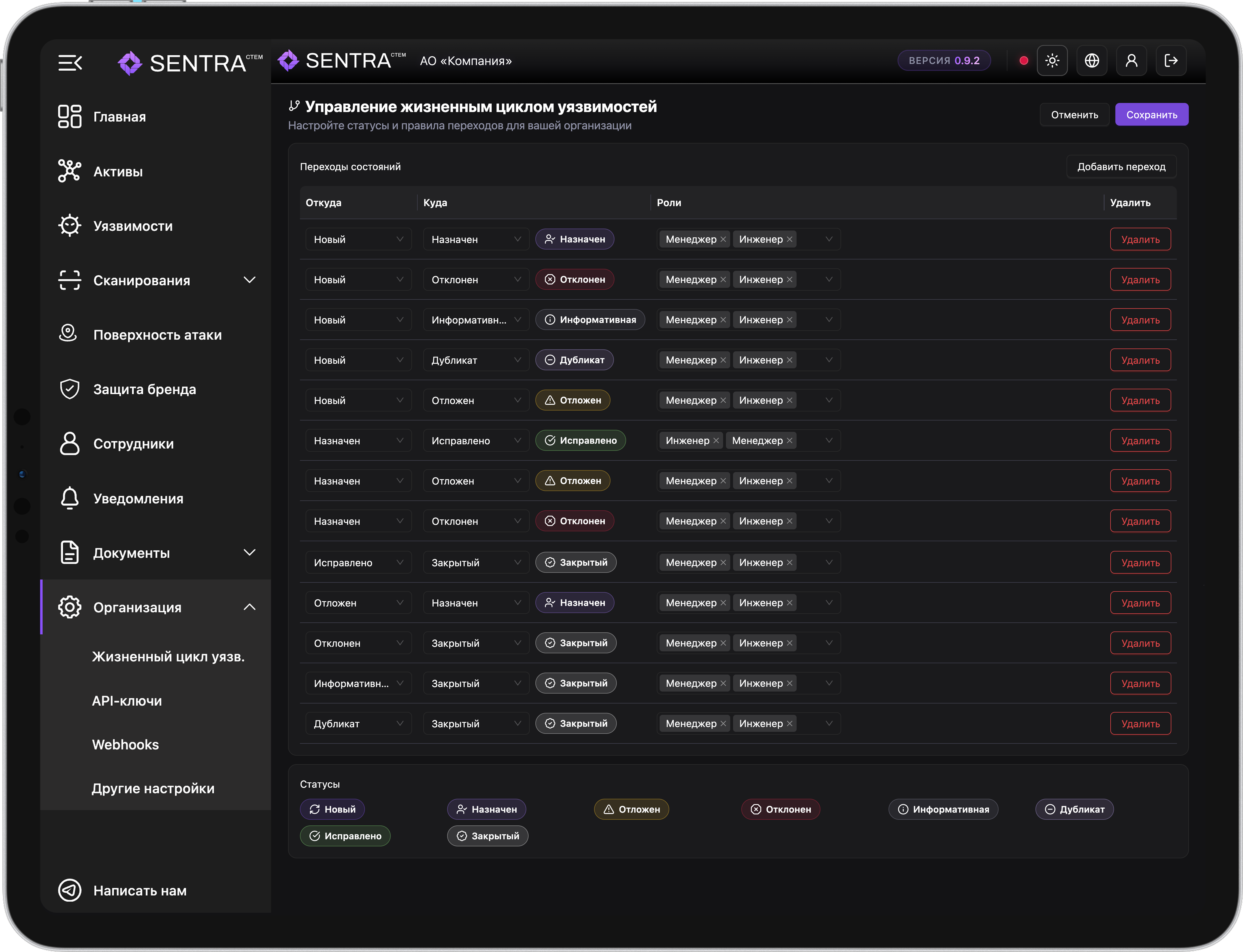
CTEM (Continuous Threat Exposure Management) is a continuous cycle of managing external threats that includes not only finding vulnerabilities, but also prioritizing them, manual verification, fix validation, and continuous monitoring of changes.
The price depends on the number of IP addresses and domains to be continuously monitored, as well as additional options as requested. Access is subscription-based, usually for 1 year.
Currently the platform is deployed in Yandex Cloud within the Russian Federation. On-premise option is under development.
Yes. Platform results are available via API. We can also integrate with your internal systems.
You can automatically verify the fix from your personal account. Our security experts additionally verify the fix and check for possible bypasses. The continuous monitoring cycle then continues.
Asset and security threat discovery is performed daily; passive reconnaissance weekly.
Submit a request — we will activate a free 1‑month pilot for you.